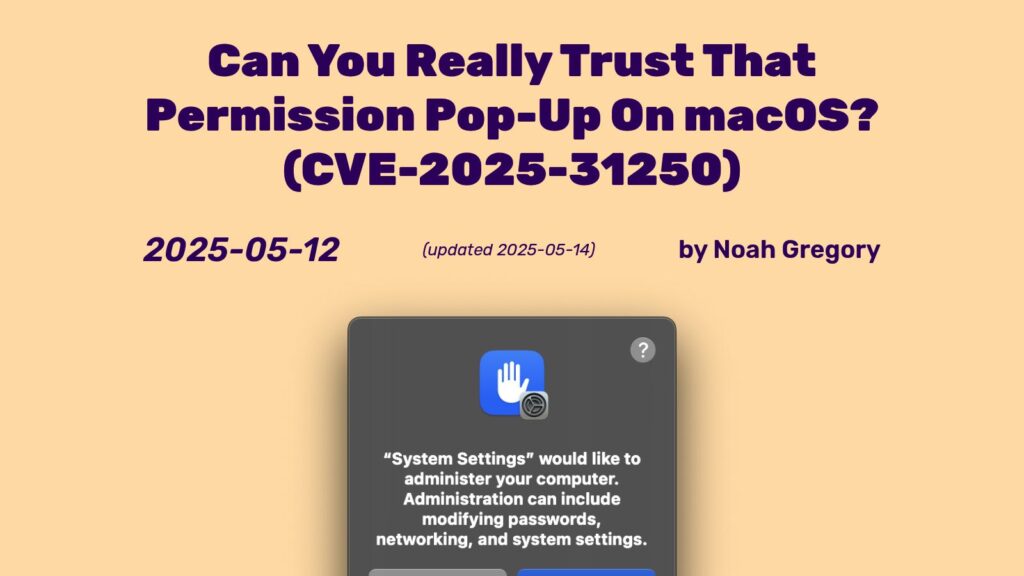
Can You Really Trust That Permission Pop-Up On macOS? (CVE-2025-31250)
macOS vulnerability CVE-2025-31250 allows apps to spoof permission prompts, misleading users into granting access to the wrong application. Correctly patched in macOS Sequoia 15.5, earlier versions like Ventura and Sonoma remain unaddressed. The flaw arises from incorrect handling in the TCC framework's request logic, permitting consent responses for one app while displaying prompts for another. While exploiting this requires user interaction, it poses significant risks, particularly for high-access applications like Microphone and Camera. Apple has responded slowly to the issue, but recent updates appear to address the vulnerability, enhancing overall security.