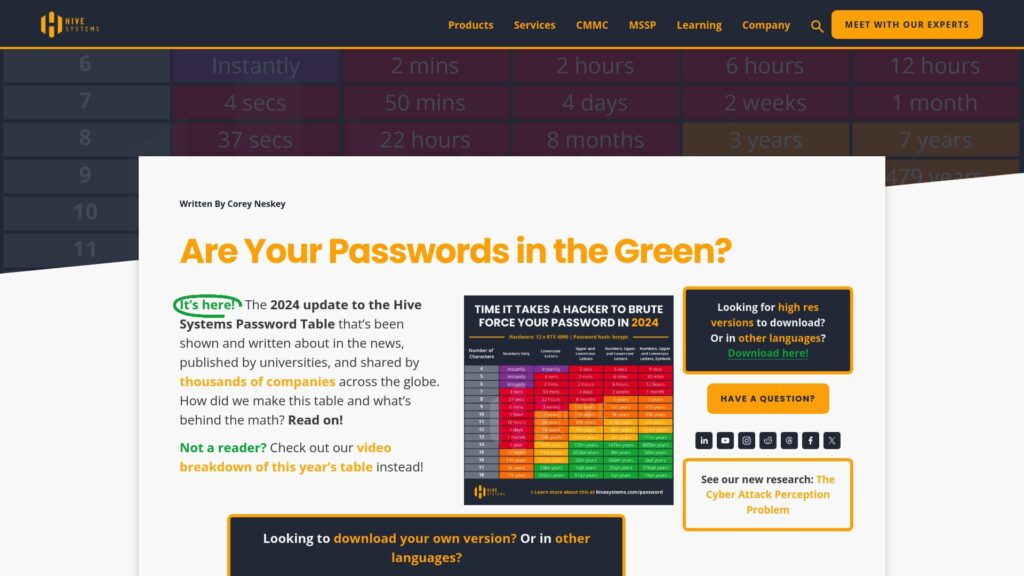
SysBumps – New Kernel Break Attack Bypassing macOS Systems Security
Researchers from Korea University exposed “SysBumps,” an attack on macOS systems using Apple Silicon. It exploits speculative execution vulnerabilities to bypass Kernel Address Space Layout Randomization (KASLR), a key security feature. By manipulating system calls and using the Translation Lookaside Buffer (TLB) as a side channel, attackers can accurately map kernel memory, achieving over 96% success in locating the kernel base address. This undermines existing kernel isolation techniques. Apple is investigating, and proposed countermeasures include TLB partitioning and code reordering. Users are advised to keep systems updated for future fixes.