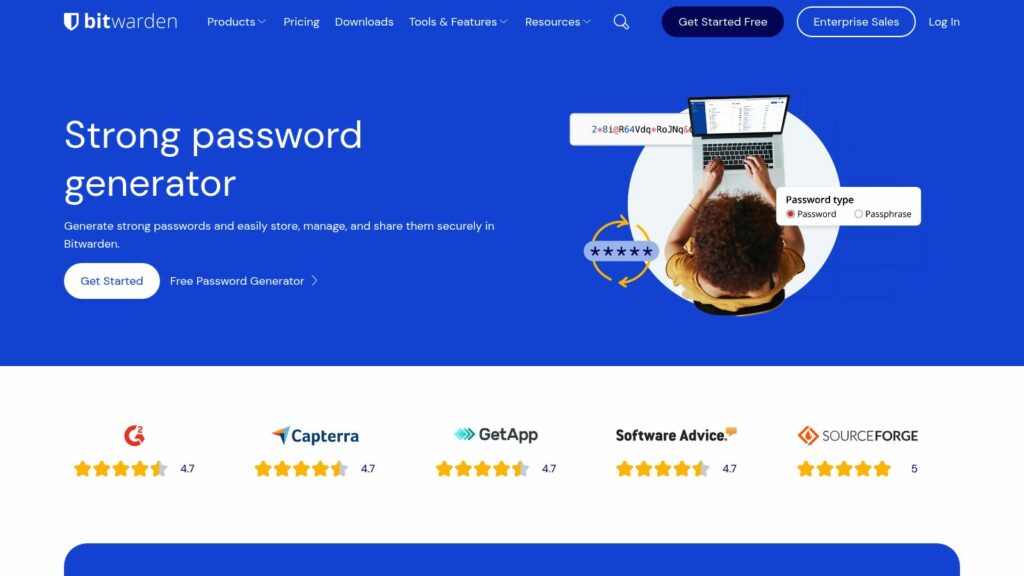
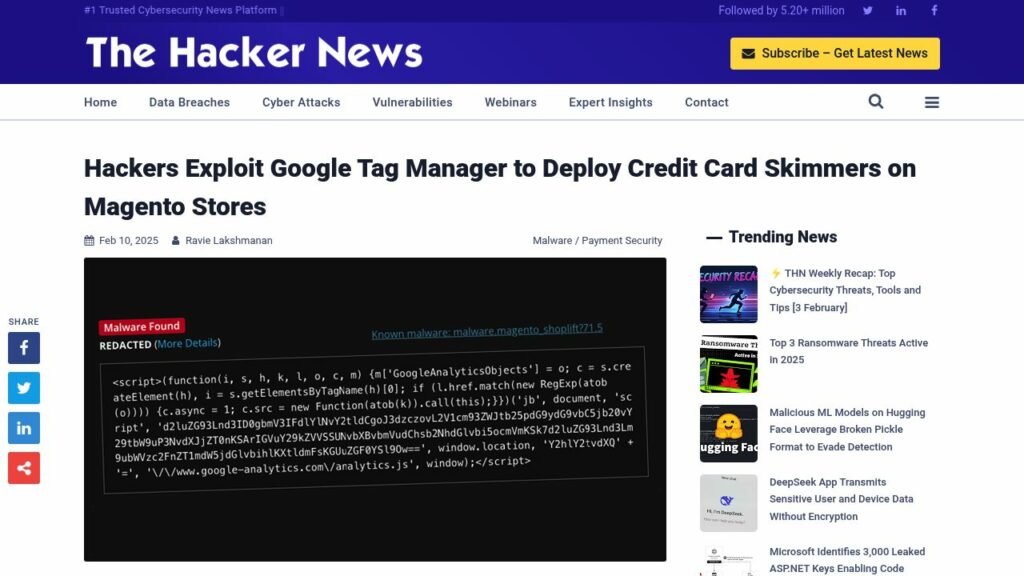
Free Password Generator
Bitwarden Password Generator: Generate strong, unique passwords easily. Strong passwords protect against hacking by avoiding personal info. Use a secure password manager like Bitwarden for managing and autofilling passwords across devices. Bitwarden offers cross-platform access and encrypted vault for securely storing passwords.