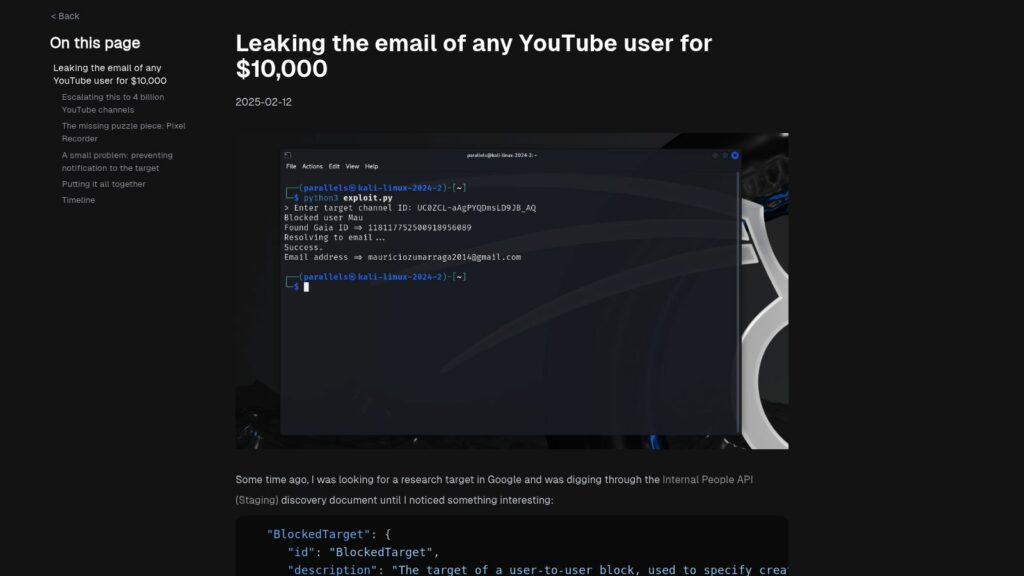
Leaking the Email of Any YouTube User for $10,000
Leaking YouTube users' emails for $10,000 is possible due to a vulnerability involving their obfuscated Gaia IDs. By blocking a user on YouTube, their Gaia ID can be obtained, which can then be resolved to an email using an old Google product, Pixel Recorder. The exploit includes steps to leak the Gaia ID from YouTube, share a recording (without triggering notifications by using an excessively long title), and obtain the email linked to the user. Despite initial patches, the issue remained exploitable and was ultimately disclosed in early February 2025 after confirming fixes and receiving a total reward of $10,633 for the findings.